Analyze the key differences between Linux and Windows servers in terms of performance, cost, security, and application compatibility. Explore VPS hosting market trends for 2025 and understand why 60% of businesses prioritize stable performance metrics. Choose the server operating system that best aligns with your business needs. Key Trends in Continue Reading
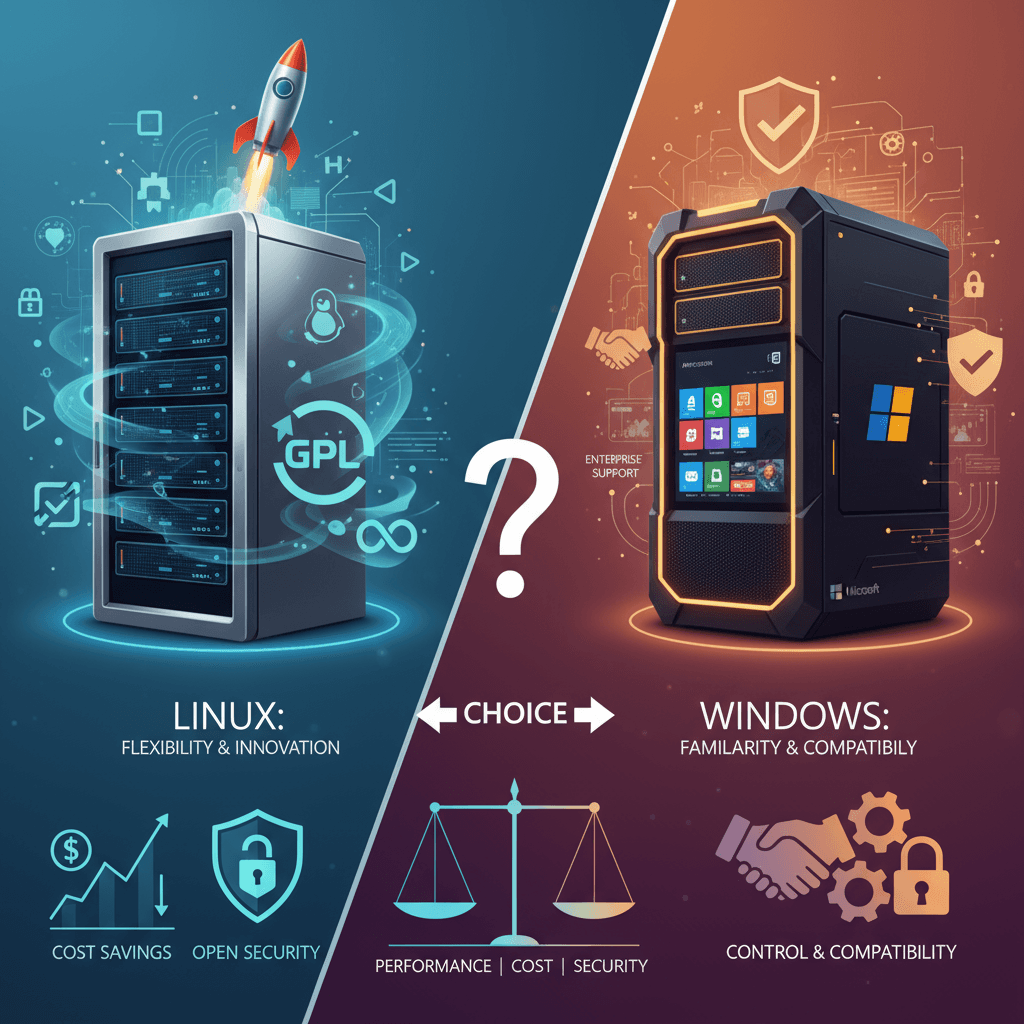
Linux Server vs Windows Server: The Ultimate Web Hosting Comparison Guide for 2025
- in Cloud Server
- by ReadySpace Hong Kong
- September 11, 2025
- No Comments
- Tags: Cost Optimization, Linux Server, Linux Server vs Windows Server, Science and technology decision-making, Server Selection, Website Performance, Window Server